December 2024
We're excited to unveil our December 2024 release, packed with powerful features and enhancements designed to make infrastructure management easier, more secure, and more efficient than ever. From expanded CLI capabilities to advanced governance tools and seamless GCP integration, this update empowers teams to streamline their workflows and maintain compliance effortlessly. Dive in to explore how StackGen continues to evolve to meet your infrastructure needs.
- What's New
- User Interface Enhancements
- Supported Resources
- What's Fixed
- Dragging and Dropping Helm Workloads Into the Topology Canvas Throws an Error
- Policy Violations for S3 Buckets Are Not Getting Resolved Automatically
- CLI Throws an Error for
NOTEMPTYCondition While Sideloading Policies - Toggle for All Azure Policies Is Not Working
- Missing Resource Icons in Governance Configurations
- Resource Restriction Policies That Are Not Part of Governance Are Displayed
- appStack Creation Fails Due to Conflicting Policies
What's New
StackGen CLI
Click to view
The StackGen CLI now supports the following actions:
provision- Provisions your appStack.destroy- Teardown your infrastructure.
To learn how these commands work run stackgen [command] --help.
Governance and Custom Policy Management
Click to view
Managing resource policies just got easier! With this release, DevOps users can create governance pre-configurations, customized policy bundles, and assign them to specific teams. This ensures your resources stay secure and compliant while giving each team exactly what they need.
-
Governance Pre-Configurations Group and assign policies to teams for consistent resource management and automatically apply policies to appStacks created by your team members. For example, assign a governance pack to a team that includes
read-onlyroles for data storage andfull-accessroles for application hosting. -
Custom Policy Options
- Custom IAM Roles: Create roles tailored to your resources, for example, allow
read-onlyandauditroles for data storage resources. - Resource Mapping: Easily map resources in your appStack, like automatically map references to a general-purpose database to your preferred service.
- Resource Restrictions: Manage the access to resources your teams can use. You can choose to limit one team to storage and compute resources while another team can use analytics tools.
- Security and Compliance Settings: Set rules for resource-specific compliance. Ensure encryption and monitoring are automatically applied to all sensitive resources.
- Custom IAM Roles: Create roles tailored to your resources, for example, allow
-
Easy Role-Based Control
- Assign configurations to specific teams or all users with just a few clicks. You can give your developers access to non-production resources, while operations teams manage production systems.
Where It Works
- Supported Clouds: All Clouds
- Supported Resources: All supported resources
With these updates, you can enforce policies without micromanaging. Teams get the access they need, and you maintain security and compliance effortlessly. Try it today and streamline your governance workflows!
GCP Integration With IAM Support
Click to view
We’re excited to announce the integration of Google Cloud Platform (GCP) into StackGen with enhancements to Identity and Access Management (IAM) functionality. Here’s what you need to know:
-
Simplified IAM Management: IAM role bindings can now be managed directly within individual resources, such as storage buckets and service accounts. This approach mirrors the GCP Console, making it intuitive for users who are already familiar with GCP.
-
Project-Level IAM Controls:
- Manage IAM roles at the project level with the flexibility to override or add role bindings.
- Create and manage custom roles with specific permissions.
Why This Matters
These changes make it easier to manage permissions while respecting existing IAM policies. The new streamlined approach reduces complexity, ensuring you have control over access without any additional steps.
How This Helps
- Consistency: The new design aligns with the GCP Console experience, making the StackGen platform more intuitive.
- Future Updates: Going forward, all new GCP resources with IAM capabilities will follow this user-friendly approach..
Custom Resource Versioning
Click to view
We’re excited to introduce a new Custom Resource Versioning feature that lets you manage and upgrade custom resources in your topologies easier than ever!
Start Simple, Upgrade Anytime: Create the initial version of a custom resource, then upgrade it seamlessly when needed.
How It Works
- Automatic Mapping: Attributes that haven’t changed are carried over automatically.
- Upgrade Action: Apply the new version with the click of a button.
- Attribute Updates: You can add, update, or delete any attribute of an existing custom resource and create a new version. Doing so lets you maintain multiple variants of your custom resource.
- Switch between versions: You can switch between various versions and revert to the older ones.
For a visual walkthrough, check out the section on custom versioning.
Seamless Connections for Cloud Resources
Click to view
We’ve made it easier than ever to manage your cloud resources by introducing automatic resolution for resource and compute dependencies.
- Automatic Dependency Resolution: When a compute instance (like an ECS task) is linked to a resource (like Dynamo), or when two resources connect (such as Athena and S3), these relationships are automatically recognized and resolved with the relevant details.
- Simplified Environment Variables: If dependencies are set using environment variables, you only need one variable to establish the connection.
Supported Platforms and Resources
- Cloud Platforms: AWS and Azure
- Compute Types: ECS tasks, Helm charts
- Resources: All currently supported resources
With these updates, managing dependencies in your cloud infrastructure is easy and more intuitive than ever. For a visual walkthrough, check out the section on Connections for Cloud Resources.
Enhanced Helm Support
Click to view
Enhanced Helm Support in Topology Canvas
We’ve made enhancements to the Topology canvas to enable you to manage K8 Helm resources more easily and efficiently.
-
Edit Workload Resource Bundles: You can now edit resource bundles directly on the topology canvas, including adding or deleting resources within a resource bundle. This gives you the flexibility to manage and update shared configurations across multiple deployments with ease.
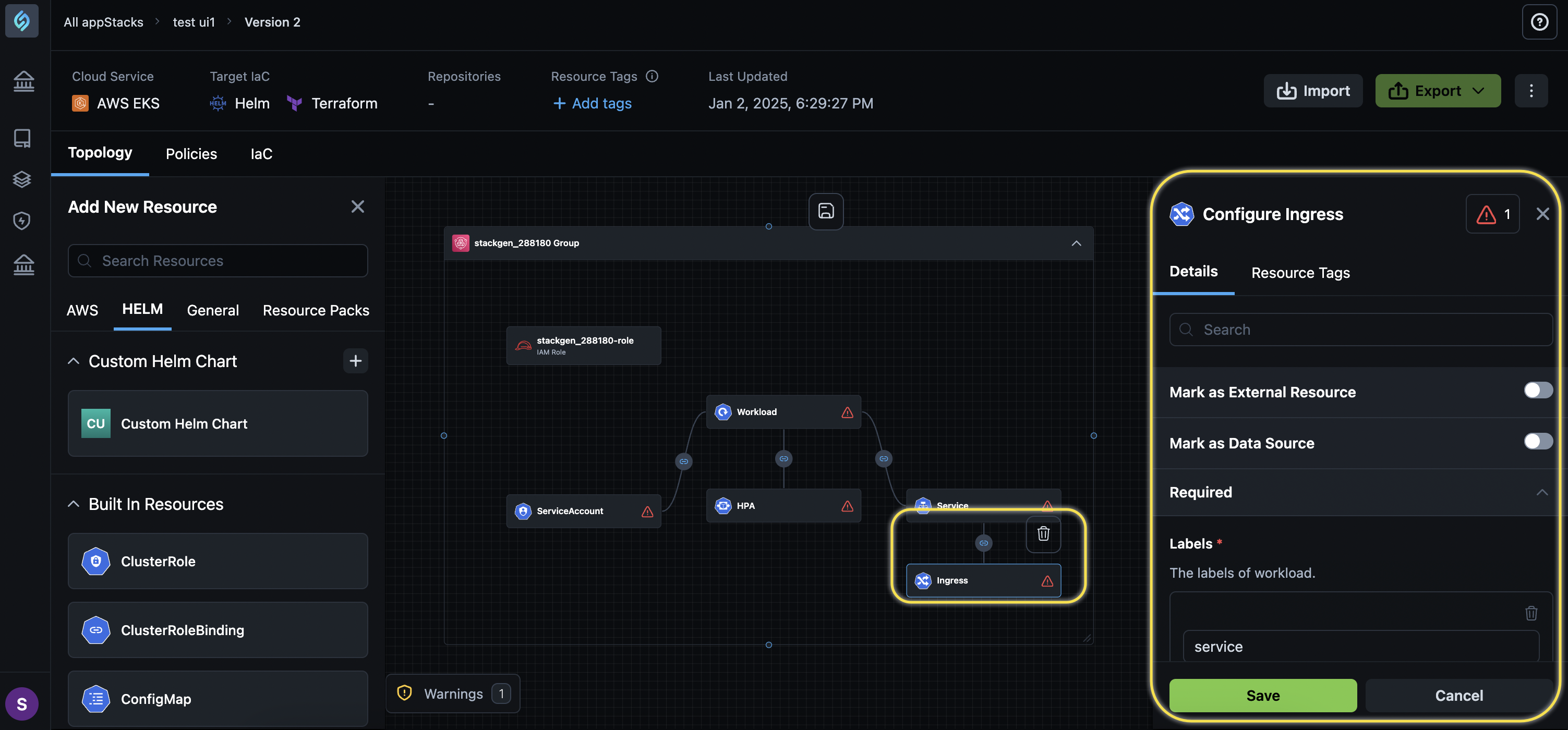
-
Share Configurations Outside Your K8 Resource Bundle Deployments: Kubernetes (Helm) deployments can now have configurations, such as Ingress, Horizontal Pod Autoscaler (HPA), and Service Accounts outside or within the resource bundle. This helps streamline resource management by reusing common settings across different workloads.
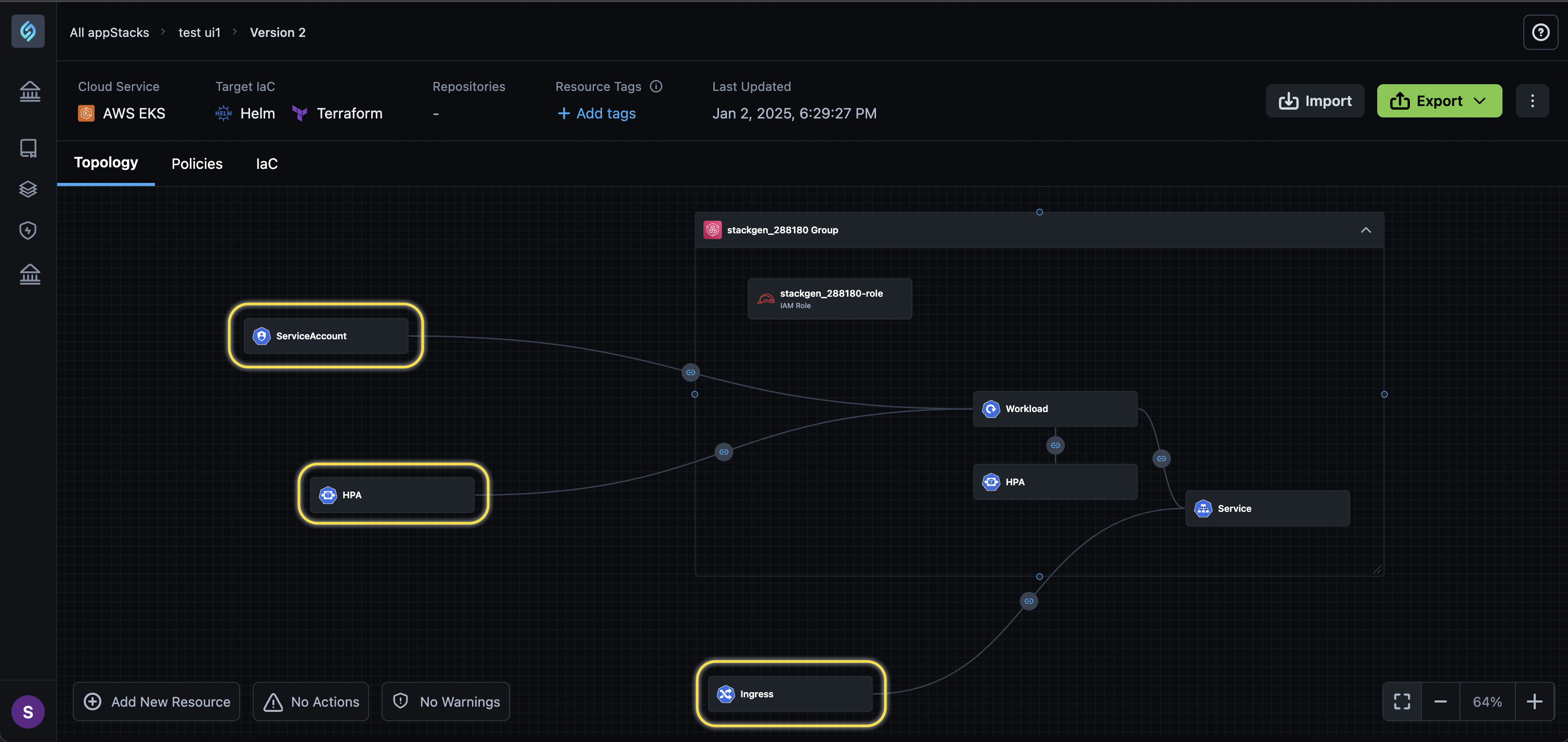
Support for Adding Helm Charts Through Repository
We have enhanced the Add Custom Helm Chart feature to support importing custom charts from your application source code repository.
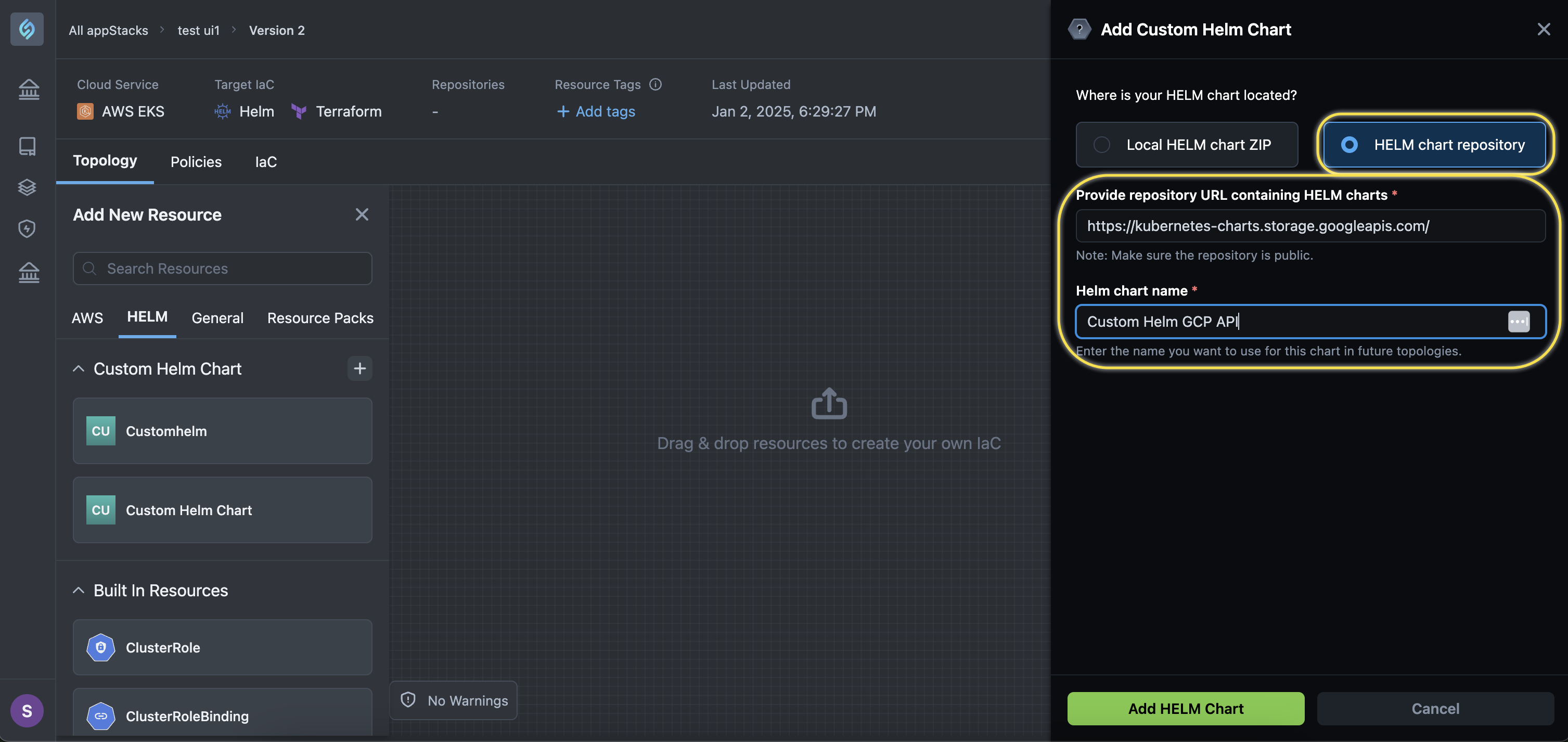
All you need is the URL of the repository that contains your Helm chart, and you're all set.
User Interface Enhancements
Enhanced Migration Topology Visibility
Click to view
To provide you with better context during migrations, we now display both the source cloud pre and post-migration topology.
Why It Matters
-
View the original resource structure and dependencies in the source cloud and understand how the topology would evolve after the migration process.
-
Side-by-Side Comparison: View both topologies within a single interface for easy reference.
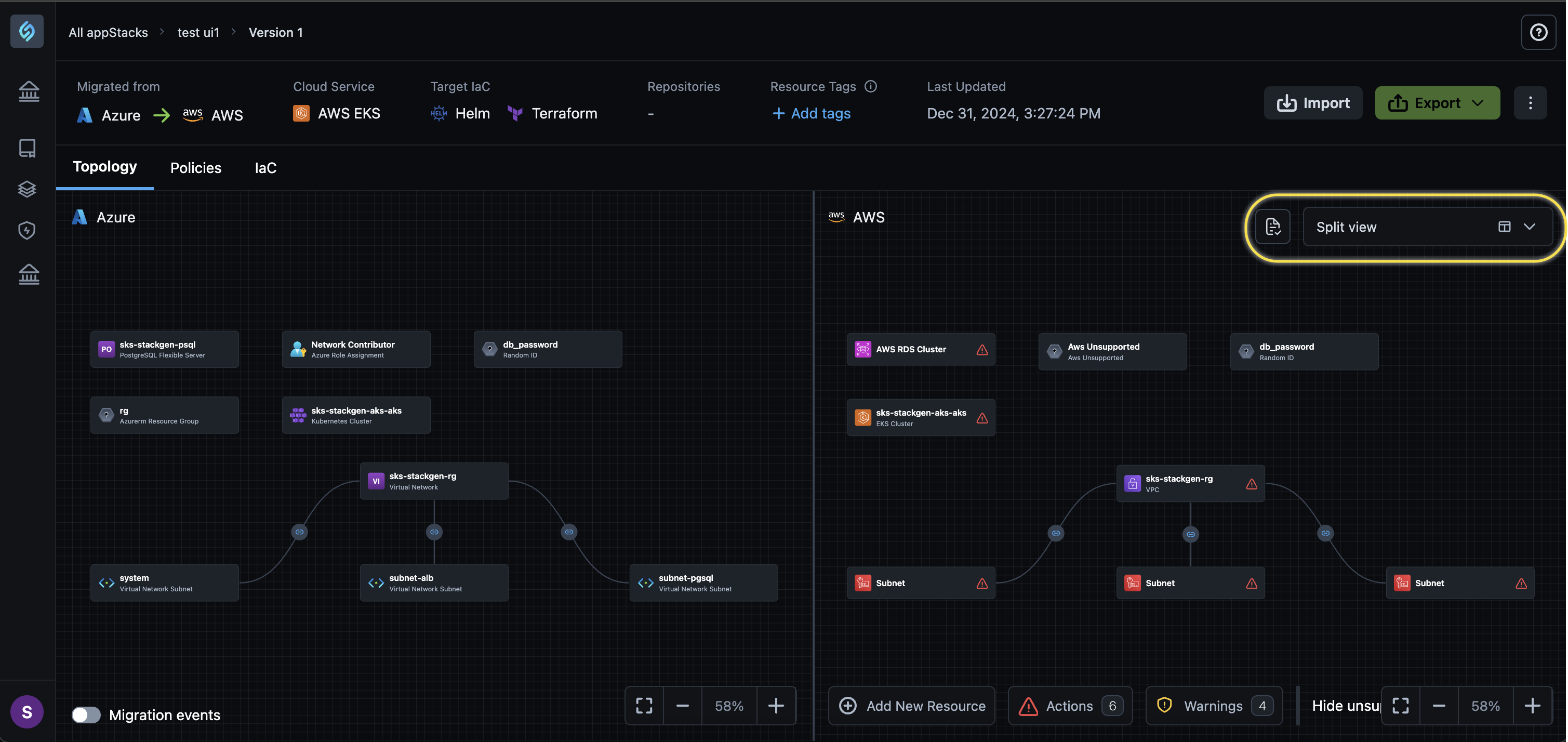
-
Improved Clarity: Identify changes and ensure your migration aligns with your expectations.
-
Simplified Troubleshooting: Quickly spot any discrepancies between pre and post-migration states.
How It Helps You
Whether you’re validating the success of a migration or planning resource adjustments, this update provides the transparency you need for a smooth and error-free cloud transition.
Custom Resource Versioning
Click to view
The new Custom Resource Versioning feature simplifies managing and upgrading resources. You can start with an initial version and upgrade it easily whenever needed. Unchanged attributes are automatically carried over, and upgrades can be applied with a single click. You can also add, update, or delete attributes, maintaining multiple versions of your custom resource, and effortlessly switch between or revert to older versions as needed. For more information, refer to the Custom Resource Versioning section of the Release Notes.
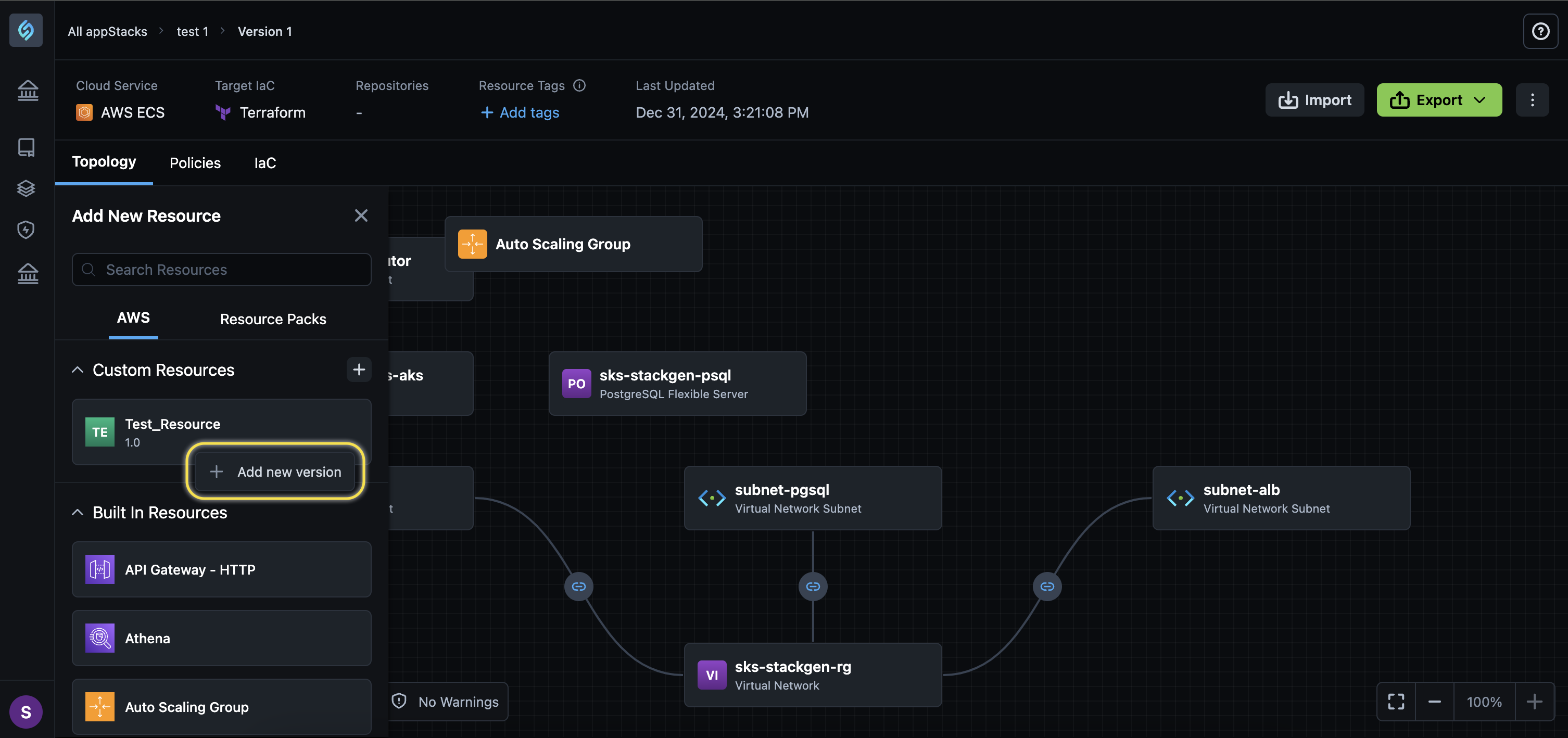
Create a New Version of Your Custom Resource
Here's how you can create a new version of your Custom Resource:
-
Navigate to the Topology editor of your appStack.
-
Click the + Add New Resource button at the bottom-left corner.
-
Click on the gear icon next to your Custom Resource. To create a new Custom Resource, refer to the article .
-
Click + Add New Version button.
-
You can modify your resource as required and then click Create Resource Version.
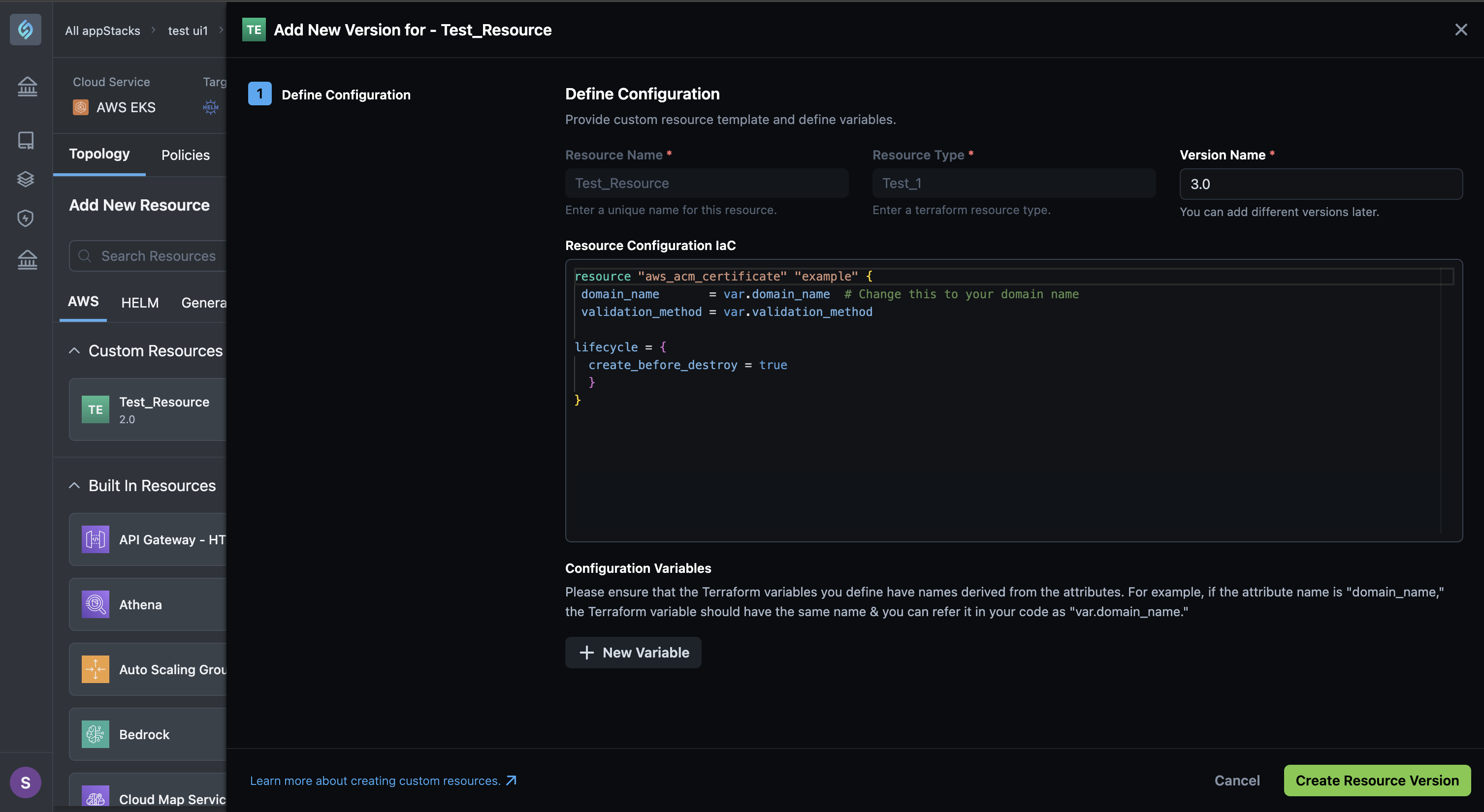 note
noteYou can change the default Version Name to create your own. For example, you can switch from 1.0, and 2.0 to 1.0, 1.1, 1.3, etc.
-
Once saved, you can navigate back to the Topology editor and click your Custom Resource to open the details panel.
noteAdding a newly versioned custom resource will not automatically update the version of a previously added custom resource. You will need to manually switch to the newer version. Alternatively, you can add the same custom resource with varying versions to your resource topology.
-
Click the dropdown next to the Resource Name, to select and switch between your custom resource versions.
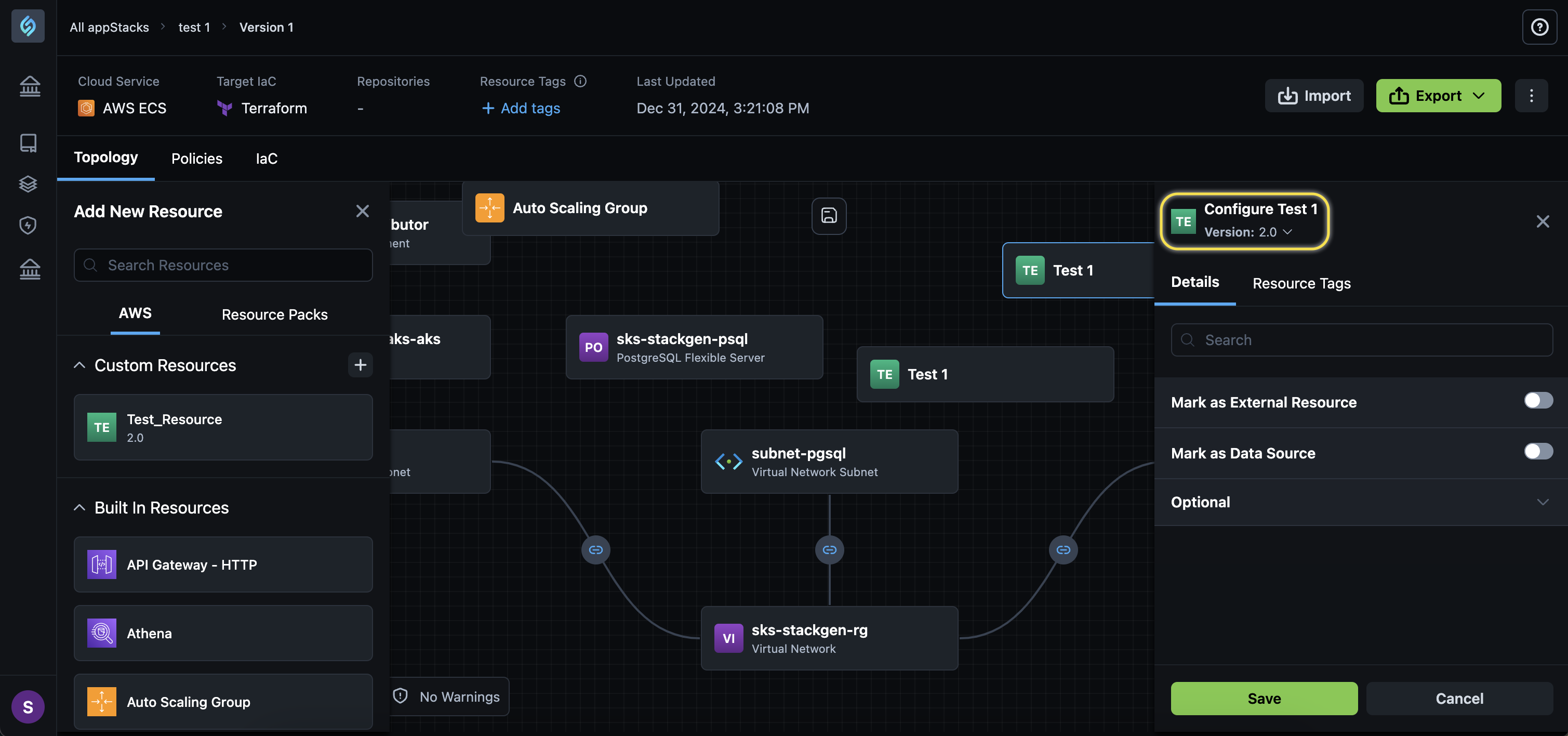
-
Click Save.
Connections for Cloud Resources
Click to view
Now you can create attribute dependencies for your Cloud Resource Connections. To know more about this enhancement in detail, refer to the section Connections for Cloud Resources
You will see connection icons next to a Resource Connection
StackGen will automatically recognize dependencies and relationships between various compute instances or resources and resolve your connections with relevant details.
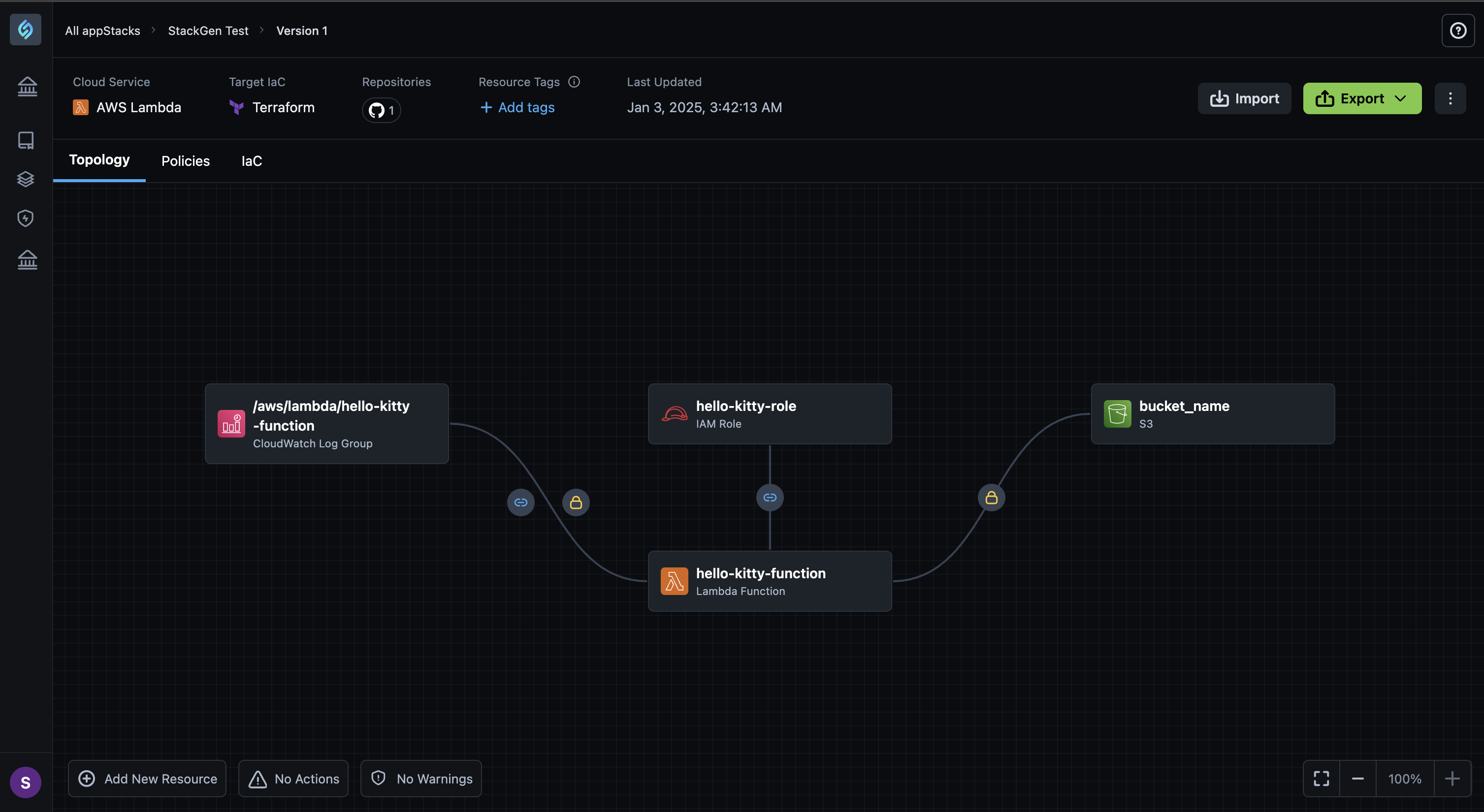
If dependencies are set using environment variables, you only need one variable to establish the connection. You can configure references and also select the attribute values for each of the connections.
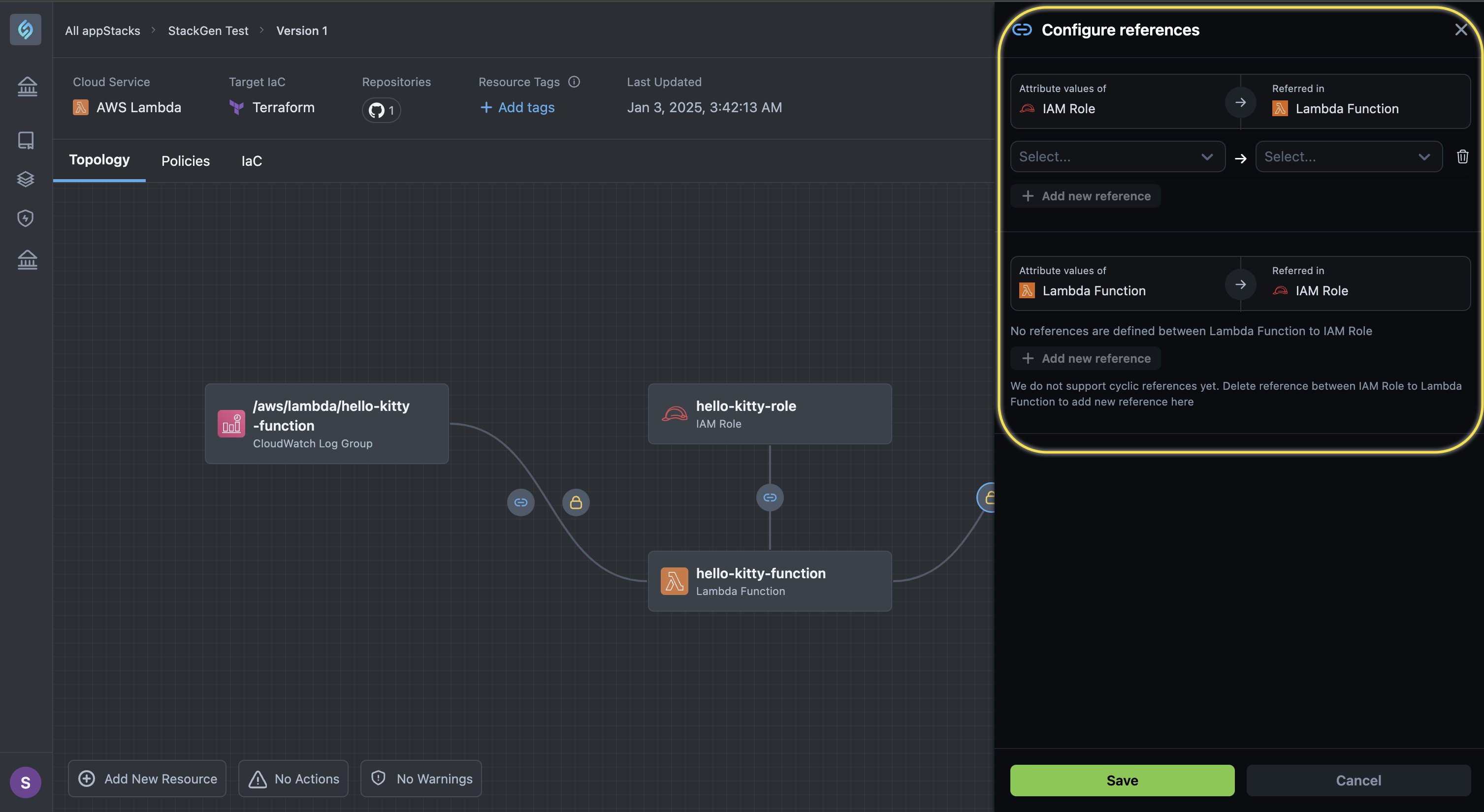
Supported Resources
Azure
Click to view
We now support the following Azure technologies:
| Resource Name |
|---|
| Log Analytics Solution |
| Log Analytics Workspace |
| Kubernetes Cluster |
| Monitor Autoscale Setting |
| Availability Set |
| Linux Virtual Machine Scale Set |
| Proximity Placement Group |
| Virtual Machine |
| Virtual Machine Scale Set |
| CosmosDB Account |
| CosmosDB SQL Container |
| CosmosDB SQL Database |
| MySQL Flexible Server |
| PostgreSQL Server |
| Redis Cache |
| Databricks Workspace |
| EventHub |
| Application Gateway |
| Load Balancer (LB) |
| Subnet |
| Virtual Network |
Refer to the section on Supported Resources to know the resources supported by StackGen.
What's Fixed
Dragging and Dropping Helm Workloads Into the Topology Canvas Throws an Error
Click to view
We've fixed the issue with dragging and dropping a Helm Workload into the Topology canvas. Previously, dragging and dropping Helm Workloads that were part of appStacks created with Governance, with a Resource Restriction Policy would throw an error: Forbidden - Export not allowed for resource types [group] in this appstack.
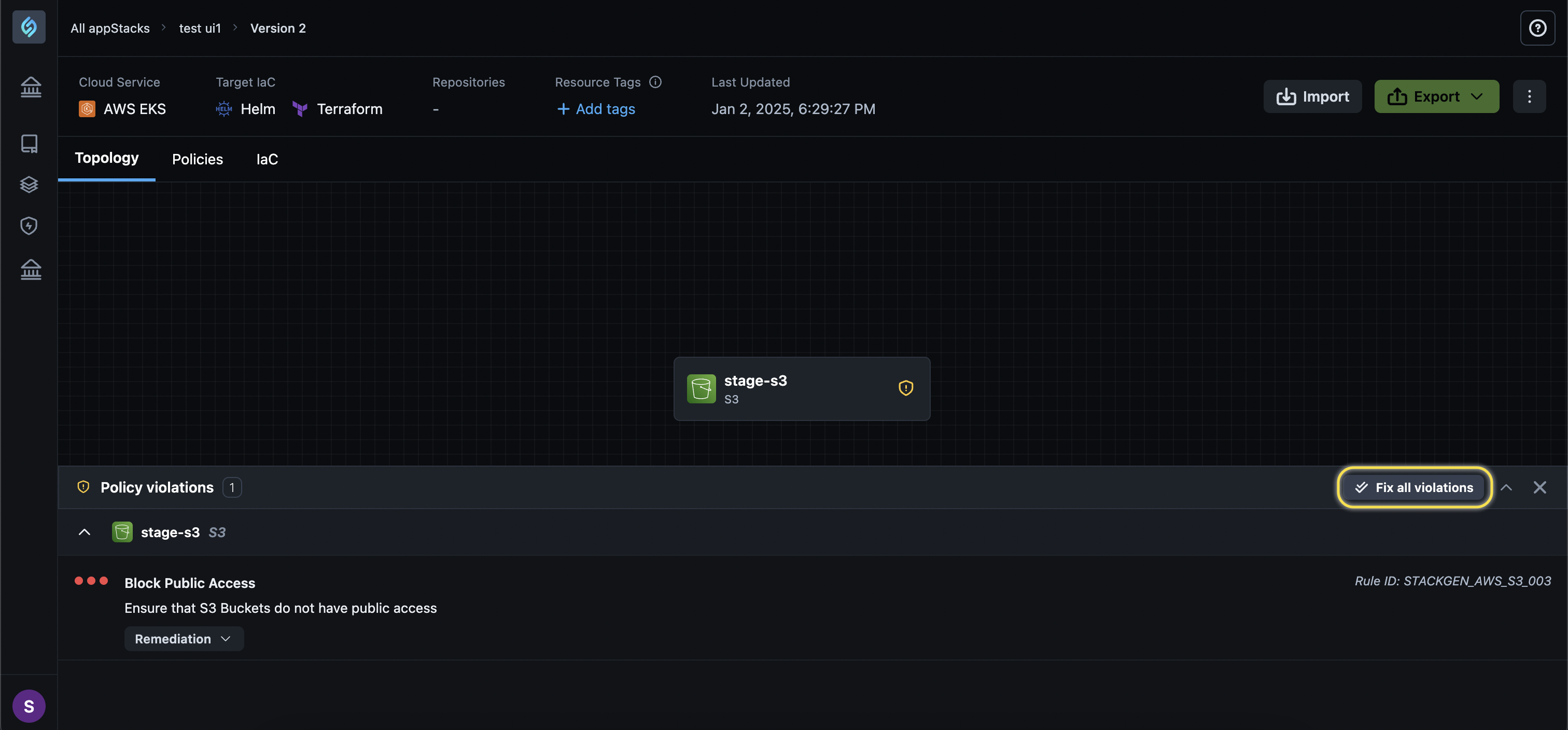
Policy Violations for S3 Buckets Are Not Getting Resolved Automatically
Click to view
Policy violations for S3 Buckets will now get resolved automatically when you click Fix all violations from the Policy Violations Panel under the Warnings section.
CLI Throws an Error for NOTEMPTY Condition While Sideloading Policies
Click to view
We've updated the validation logic to allow the NOTEMPTY operator without a value. Previously, Policies with an empty NOTEMPTY operator were not being uploaded because of the validation error.
Sample Policy
{
"attribute": {
"name": "enable_versioning",
"default": true,
"data_type": "bool"
},
"operator": "NOTEMPTY",
}
Sample Error
Error:
{"msg":"Invalid policy file","errCode":"","extras":["error validating policy schema [0.rules.0.conditions.1: value is required]"]}
ERROR security rules upload failed!
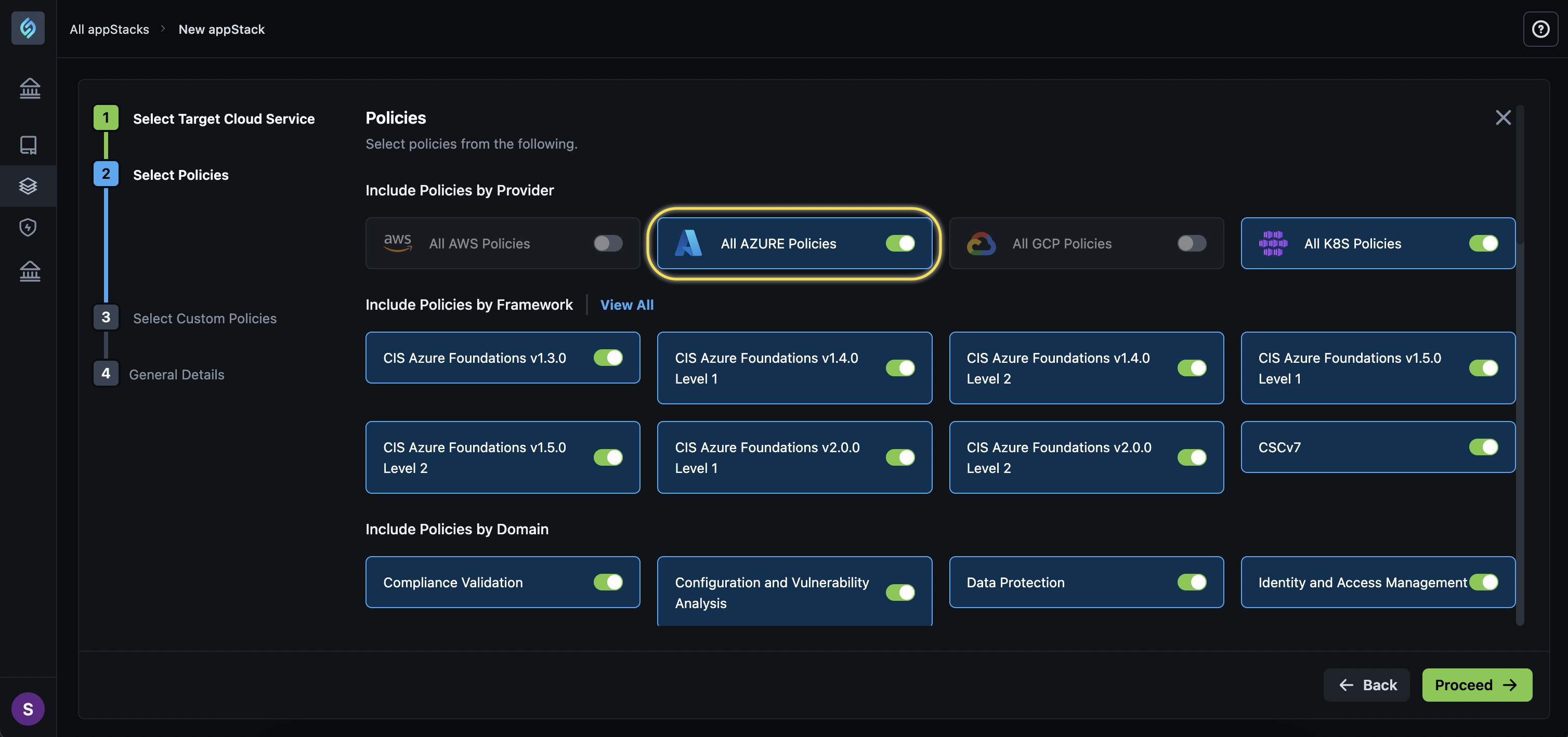
Toggle for All Azure Policies Is Not Working
Click to view
We have resolved the issue with the toggle for allowing you to seamlessly enable all Azure policies. Previously, the toggle to enable all Azure policies at once was not working. You would need to enable all policies manually.
Missing Resource Icons in Governance Configurations
Click to view
Resource Type icons are now displayed for all resources while creating governance configurations on the Policies page for a more consistent visual experience.
![]()
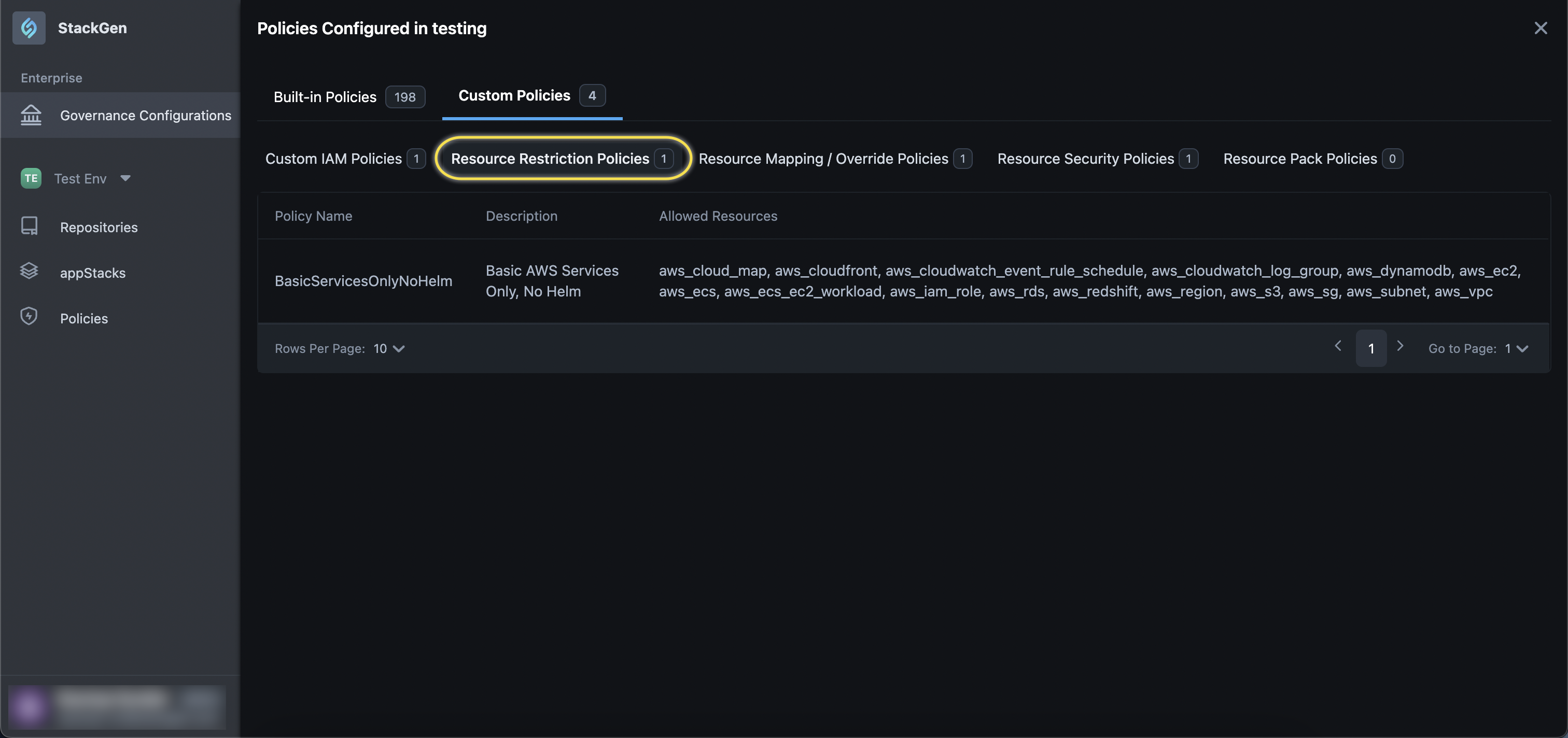
Resource Restriction Policies That Are Not Part of Governance Are Displayed
Click to view
We have updated the display logic to show only Resource Restriction Policies that are part of the active Governance Configuration while excluding others from the list. Previously, Resource Restriction Policies that were not part of the Governance Configuration, were being incorrectly displayed as included while viewing the list of Included Policies.
appStack Creation Fails Due to Conflicting Policies
Click to view
We have enhanced the appStack creation process to ensure that all security policies defined in the Governance Configuration are included, even if they don't match the selected deployment strategy (e.g., AWS Lambda or AWS ECS).
Previously, while creating an appStack with a governance configuration, certain security policies were excluded due to the selected cloud service which caused the appStack creation process to fail due to these missing policies.